Fake SSH Server
7th April 2015
I've started from an existing tiny ssh server implementation and I've changed it into a fake ssh one (fakesshd.tar.gz).
The server recognizes the following Unix commands and outputs a plausible output for each:
- "busybox" "cat" "cd" "chmod" "df" "echo"
- "free" "gcc" "grep" "id" "ifconfig"
- "killall" "logout" "ls" "ll" "lscpu" "make" "mv"
- "netstat" "nproc" "ps" "pwd"
- "uname" "uptime" "w" "wget" "whoami"
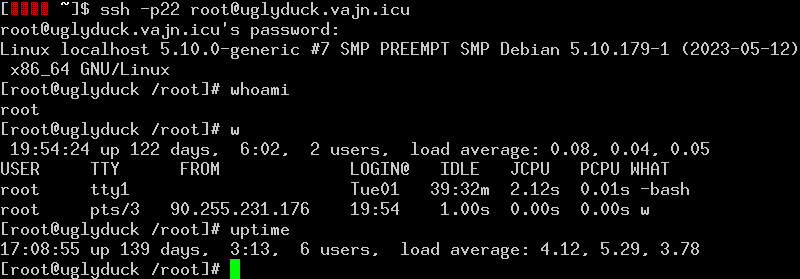
I have installed this fake service on a few machines (including this one) as a honeypot SSH server (fakessh). To log in as "root" you need to enter a password which starts with "1". The vast majority of logins are done by automatic scripts which search for weak passwords and repeatedly execute the same commands even when they "log in" with different passwords. Since mid 2018 I've noticed ssh login attempts to non-standard ports like 2222 and 1022 intensifying.
